38 symantec antivirus best practices
Citrix World and Symantec Best Practice Notes and configurations Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Symantec\Symantec Endpoint Protection\SMC\. 3. Create a new key named Virtualization. 4. Under Virtualization, create a key of type DWORD named IsNPVDIClient and set it to a value of 1. Step 4. In Symantec Endpoint Protection Manager, enable Tamper Protection again. Is any virus protection software needed for Red Hat Enterprise Linux? There are also some good security practices to follow to make sure a system is safe: Keep a system updated so all patches and security updates are installed. A subscription to Red Hat Subscription Management (RHN) will help keep a system updated. Run a local firewall on the system, such as iptables, to block any unused ports.
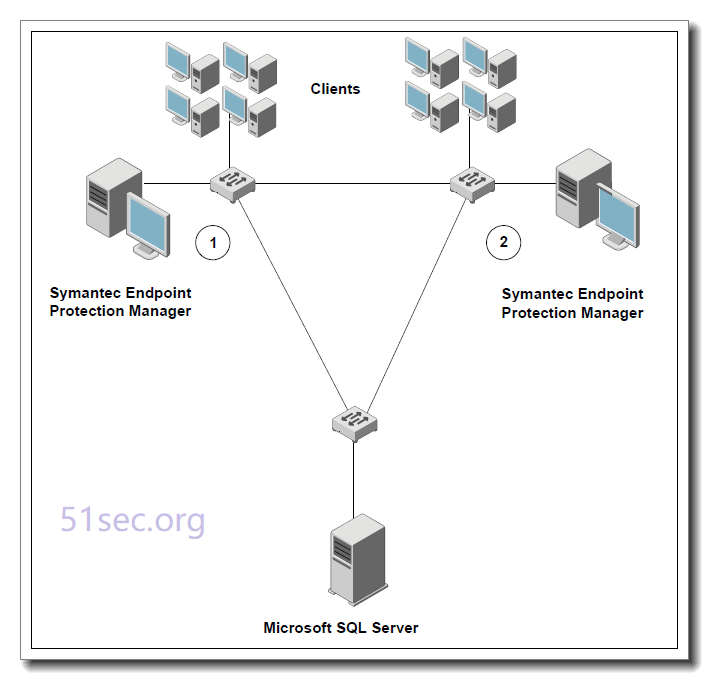
Best practices for SQL Server | Endpoint Protection Best Practices guide for Installing the Symantec Endpoint Protection Manager with a SQL Server 2005 Database Best Practices guide for Installing the Symantec Endpoint Protection Manager 11 RU5 with a SQL Server 2008 Database

Symantec antivirus best practices
How to choose antivirus software to run on computers that are running ... When you configure your antivirus software settings, make sure that you exclude the following files or directories (as applicable) from virus scanning. This improves the performance of the files and helps make sure that the files are not locked when the SQL Server service must use them. PDF Dell EMC Isilon: Antivirus Solutions - Dell Technologies Best Practices Dell EMC PowerScale: Antivirus Solutions Best practices for performance and sizing Abstract This white paper provides best practices for planning a Dell EMC™ PowerScale™ scale-out storage solution that requires antivirus capabilities as well as the Internet Content Adaptation Protocol (ICAP) to manage scanning with Endpoint Protection - Symantec Enterprise - Broadcom Inc. SEP 12.1 RU5 introduced a managed SEP for Linux client in September 2014. Details can be found in New fixes and features in Symantec Endpoint Protection and Network Access Control 12.1.5 and Symantec Endpoint Protection 12.1.5 for Linux Client Guide. The use of this new, managed SEPFL client is highly recommended over the legacy SAVFL client.
Symantec antivirus best practices. Symantec Antivirus Best Practice for Hyper-v 2012 R2 Cluster Look for products or settings that allow for randomization of full disk scans on the VMs or do not do full disk scans and only keep the real time scanners active on the VMs for incoming writes. 2. Watch for Antivirus products that update all the VMs at the same time. Best practices for anti-virus on SQL Server - The Spiceworks Community Antivirus Best practices for anti-virus on SQL Server Posted by promonathan on Sep 27th, 2017 at 1:23 PM Solved Antivirus Hello, Team- I have a question regarding installation of antivirus on production SQL server (s). Citrix Guidelines for Antivirus Software Configuration In high-security environments, organizations should consider scanning on both read and write events to protect against threats that target memory, such as Conficker variants. Scan local drives or disable network scanning. MDE Antivirus Configuration Common Mistakes and Best Practice Best Practices for AV Policy Settings: You may wonder what is the best Scan types for your daily scheduled scan on all systems, the Full Scan is for investigation of virus attack on the system, for the weekly or daily scheduled scan, it should be good and sufficient with quick scan.
Pros and Cons of Symantec Endpoint Security 2023 - TrustRadius Symantec Vendor need to improve the Technical support case handling process. High priority case need to given more priority. Verified User Professional in Information Technology Automotive Company, 1001-5000 employees Real Time - firewall detection Can be a pain for end users when trying to install new application on their workstations Incentivized Norton vs Symantec| Which one is the best Antivirus Software Norton 360 Delux 3 Devices. Norton 360 Delux. $16.48/year/device. $24.69/year/3 devices. $48.07/year/5 devices. And off-course like 5000+ more software you can access free trials for both Norton and Symantec Endpoint Protection here at AnyTechTrial.Com. In conclusion, we would say that Norton Antivirus is one of the most efficient and effective ... LogicMonitor Security Best Practices | LogicMonitor Set strong passwords for administrative accounts Change other default passwords as applicable Disable guest accounts and unnecessary network services Protect the system from the public internet using either a host-based or network-based firewall Stay current with vendor-provided security patches Anti-Malware Exemptions Manage antivirus settings with endpoint security policies in Microsoft ... Intune Endpoint security Antivirus policies can help security admins focus on managing the discrete group of antivirus settings for managed devices. Antivirus policy includes several profiles. Each profile contains only the settings that are relevant for Microsoft Defender for Endpoint antivirus for macOS and Windows devices, or for the user ...
What's new for Symantec Endpoint Protection 14.3 RU6? The Symantec Endpoint Protection Manager (SEPM) sends an email alert when a system administrator initiates SEPM enrollment with the Symantec Integrated Cyber Defense Manager (ICDm) cloud console. ... See information on the best practices for using Symantec Endpoint Protection beyond just antivirus: Best practices for stopping malware and other ... Good cyber hygiene habits to help stay safe online | Norton Step 2: Use network firewalls Using a network firewall is another key habit for maintaining good cyber hygiene. Firewalls are a first line of defense in network security by preventing unauthorized users from accessing your websites, mail servers, and other sources of information that can be accessed from the web. Step 3: Update software regularly Best practices for Symantec Endpoint Protection - Support Portal Best practices for firewall policy settings for remote clients Security Strengthen your overall security posture and protect your network against malicious threats and attacks. Recommended security settings for Endpoint Protection Ransomware protection and removal with Endpoint Protection Tech Paper: Endpoint Security, Antivirus, and Antimalware Best Practices Available performance optimization strategies and approaches are different for various antivirus vendors and implementations. One of the most common and effective approaches is to provide centralized offloading antivirus scanning capabilities.
Antivirus Best Practices For Complete Cybersecurity Below are antivirus best practices that can guarantee complete system protection, ensure normal day-to-day system functioning, detect and eliminate threats when followed to the letter. READ ALSO: Best Antivirus For 2022. Antivirus Best Practices Limit physical access to computers to few authorized users. Limiting access to computers can greatly ...
Antivirus Considerations in a VMware Horizon Environment Ensure that you keep golden images regularly updated with new antivirus software versions and signature files. Scan VMware View Composer persistent disks—formerly called user data disks (UDD)—for viruses on a regular basis. Because this type of disk is persistent, a refresh or recompose operation will not remove any viruses.
How to uninstall Symantec Endpoint Protection - Best Practices - Spiceworks To have the Latest Version of Symantec CleanWipe Tool, you may need to Create / Open a Case with Symantec Technical Support. Check the Procedures to open the Case in Step 3. If you are not able to open a case, there are manual removal documents available that can help you with removing all traces of the SAV/SEP product.
Ransomware mitigation and protection with Symantec Endpoint Protection Best practices to mitigate ransomware Hardening Your Environment Against Ransomware In addition to enabling SEP protection, follow additional steps to avoid ransomware infection. Steps to avoiding ransomware Step Action 1. Protect your local environment Ensure you have the latest version of PowerShell and that you have logging enabled.
Symantec Endpoint Protection Recommended Best Practices for Securing an ... Symantec strongly recommends disabling Autorun functionality for USB devices and network drives. Close open or unnecessary shares Many malicious threats attempt to enumerate all available file shares, either on other desktop systems or file servers, in order to spread to those systems.
Bitdefender vs Symantec| Which one is the best Antivirus Software In a nutshell, we can say that Bitdefender offers Device control, web filtering, exchange mail protection, intrusion detection, and free 24-hour support, and many more services. While Symantec software is more than antivirus as it provides end-to-end protection of laptops, desktops, servers, mobile devices, messaging, and Web infrastructures ...
Should I install an AV product on my domain controllers? It should run on servers too, for two reasons: 1) they're the most critical computers in your environment, much more than client systems, and 2) they're no less at risk only because nobody actively uses (or at least should not being actively using) them for surfing the web: there's plenty of malware which can automatically spread across your …
Antivirus Considerations for VMware Horizon 7 One of the consequences of running antivirus software is that operating system performance can suffer. There is a balance between an acceptable level of security and an acceptable level of performance, and this varies from one environment to the next. This article discusses the use of antivirus software in a VMware Horizon 7 environment, and changes that can be made to improve performance ...
Recommended antivirus exclusions for Hyper-V hosts Configure the real-time scanning component within your antivirus software to exclude the following directories, files, and processes. Note If you are using Windows Defender as an anti-malware solution on your server, you may not need to configure additional exclusions.
Antivirus Scanning Best Practices - techdocs.broadcom.com Antivirus Scanning Best Practices Content Analysis scanning behavior options allow you to set the parameters for optimal malware scanning. These options are in the Services > AV Scanning Behavior screen. The default values for antivirus scanning behavior policies are defined with security best practices in mind.
10 Cybersecurity Best Practices that Every Employee Should Know - Norton Cybersecurity best practices encompass some general best practices — like being cautious when engaging in online activities, abiding by company rules, and reaching out for help when you encounter something suspicious. Here's a deeper dive into the 10 cybersecurity best practices for businesses that every employee should know and follow. 1.
Endpoint Protection - Symantec Enterprise - Broadcom Inc. SEP 12.1 RU5 introduced a managed SEP for Linux client in September 2014. Details can be found in New fixes and features in Symantec Endpoint Protection and Network Access Control 12.1.5 and Symantec Endpoint Protection 12.1.5 for Linux Client Guide. The use of this new, managed SEPFL client is highly recommended over the legacy SAVFL client.
PDF Dell EMC Isilon: Antivirus Solutions - Dell Technologies Best Practices Dell EMC PowerScale: Antivirus Solutions Best practices for performance and sizing Abstract This white paper provides best practices for planning a Dell EMC™ PowerScale™ scale-out storage solution that requires antivirus capabilities as well as the Internet Content Adaptation Protocol (ICAP) to manage scanning with
How to choose antivirus software to run on computers that are running ... When you configure your antivirus software settings, make sure that you exclude the following files or directories (as applicable) from virus scanning. This improves the performance of the files and helps make sure that the files are not locked when the SQL Server service must use them.

























0 Response to "38 symantec antivirus best practices"
Post a Comment