40 antivirus inspection is proxy based palo alto
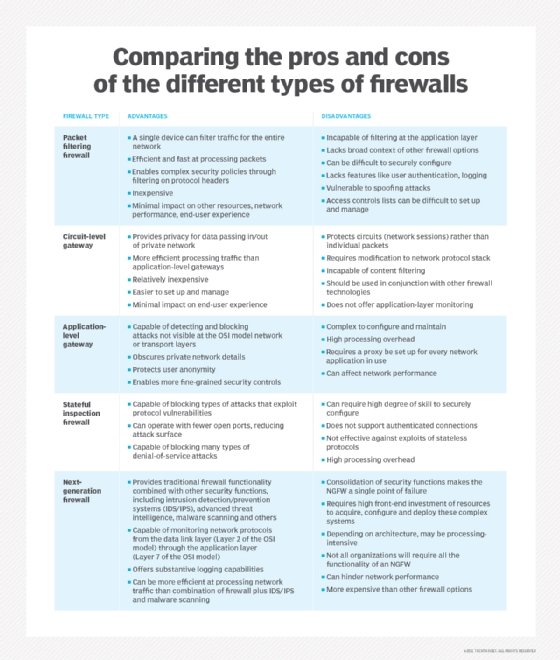
A2enmod proxy list - Fineproxy Proxy Servers from Fineproxy - High-Quality Proxy Servers Are Just What You Need. The most common device used for creating your own residential proxy is Raspberry Pi, an affordable small-sized computer that Antivirus inspection is proxy based palo alto. Http proxy injector version 1.0.1.7. What is a Firewall? The Different Firewall Types & Architectures Proxy firewalls operate at the application layer to filter incoming traffic between your network and the traffic source—hence, the name Rather than letting traffic connect directly, the proxy firewall first establishes a connection to the source of the traffic and inspects the incoming data packet.
Cisco Nexus Review, Testing & Verification of the embedded... | Indeni Taking advantage of the Cisco NX-OS architecture which is running on Linux OS, makes it easy to embed productive tools used by network administrators who are familiar with Linux-based environments.

Antivirus inspection is proxy based palo alto
types of PA firewall inspection - LIVEcommunity - 295613 PaloAlto only supports flow based inspection. ... has 2 inspection modes, the base flow mode and the proxy mode, my question is The Palo Alto firewall, ...9 answers · Top answer: Hi @o_hernandez As @MP18 correctly assumes, this is not like it is possible with fortigate ... Comparing Palo Alto Networks with Proxies Simplified Policy Management: Palo Alto Networks delivers policy-based visibility ... Apply threat inspection to each application ... Anti-virus protection.2 pages Top Threat Intelligence Platforms for 2022: Compare Solutions Palo Alto Networks Cortex XSOAR TIM. LookingGlass Cyber Solutions is an open source-based threat intelligence platform that delivers unified threat protection against sophisticated cyberattacks to global enterprises and government agencies by operationalizing threat intelligence.
Antivirus inspection is proxy based palo alto. Antivirus inspection is proxy based palo alto - proxy online Unexpectedly for me, a proxy at reasonable prices. The service works at a height. The proxy is working, I paid for 30 days, I will soon extend it. At the moment, there are quite a lot of similar services on the Internet, but I recommend this one. Tech. help works around the clock, you can communicate... Check Point Firewall Useful CLI Commands - SanchitGurukul check point. Cisco ASA. Palo Alto. Proxy. Contact. Menu. shows ospf summary information. show pbr rules. shows policy based routing rules. Unauthorized RCE in VMware vCenter - PT SWARM Previous. Swarm of Palo Alto PAN-OS vulnerabilities. Next. From 0 to RCE: Cockpit CMS. FortiGate CLI Commands Overview - World Of Security Proxy Inspection While in Conserve Mode # config system global set av-failopen [off FortiGuard connect Through a Web Proxy # config system autoupdate tunneling set address AntiVirus and IPS. diagnose test application dnsproxy 7 diagnose autoupdate status diagnose autoupdate versions.
Best Palo Alto Firewall Training by Industry Expert | Live Practice Learn Palo Alto Firewall Security courses online with Industry Experts & 100% Live Practice. Get Panorama Firewall, APP-ID, VPNs Training with Job tasks. Palo Alto Networks is a cybersecurity company that offers a wide range of products and services to protect networks from cyber-attacks. Useful Checkpoint commands | itsecworks Checkpoint is not a cli based firewall, the cli is generally (in the daily life) not used. What the admin wants, can do through the GUI. For troubleshooting purposes or just query something there are some useful commands. Just a moment... Palo Alto. Symantec. It provides these security services at the IP layer; it uses Internetwork Key Exchange (IKE) to handle negotiation of protocols and algorithms based on local policy, and to generate the encryption… Cisco WLC or AP device certificate expired... — WIRES AND WI.FI Palo Alto. Prime. Routing. For old IOS-based access points the error could look like this: [*09/09/2019 12:34:50.0099] Cert Verification FAILED with error 10 (certificate has expired) at 0 depth...
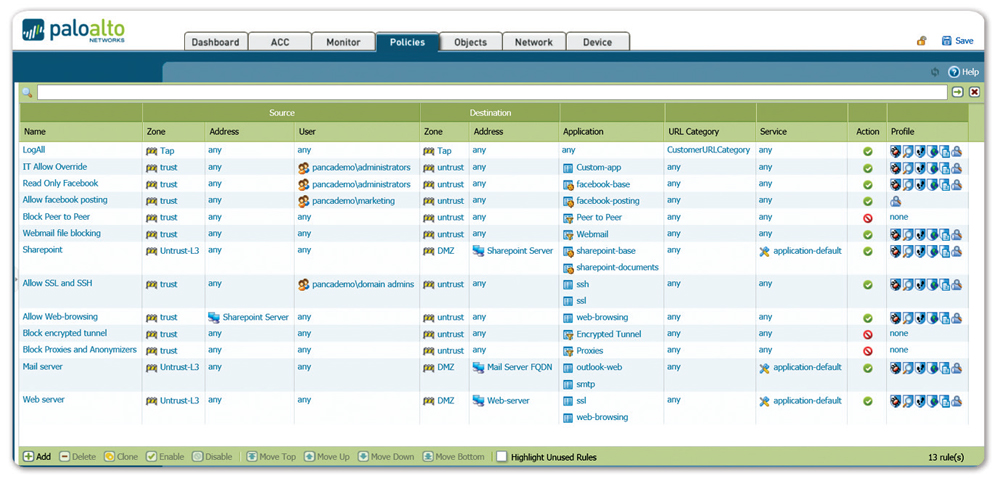
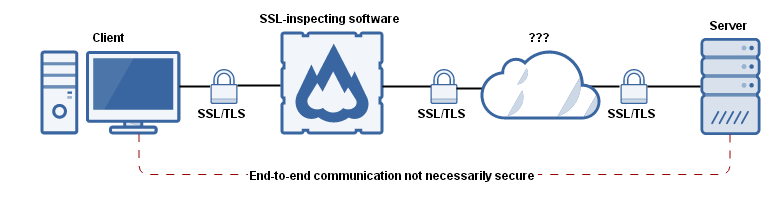
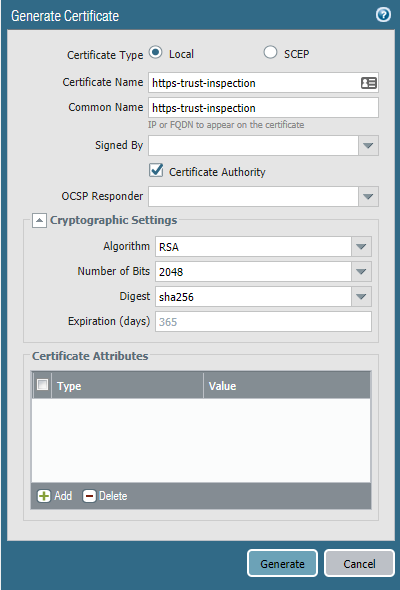
Palo Alto Networks - Wikipedia Palo Alto Networks, Inc. is an American multinational cybersecurity company with headquarters in Santa Clara, California. Its core products are a platform that includes advanced firewalls and cloud-based offerings that extend those firewalls to cover other aspects of security. PDF Microsoft Word - PCNSA study guide-bja_mg 2-19-19-bja.docx The Palo Alto Networks Security Operating Platform prevents successful cyberattacks by focusing on what matters: leveraging cloud‐based applications (see the following figure). · Full visibility and threat inspection into normally opaque web traffic through granular control over SSL decryption. Palo Alto Commands (Important) - Network Engineer Save an Entire Configuration for Import into Another Palo Alto Networks Device: > configure # save config to jobs all show jobs processed Immediately after restarting, every Palo Alto Networks firewall performs an auto-commit. This takes place in the background and can last up to 30 minutes. All about Security (13468) Palo Alto Networks platform products are commonly deployed in which five critical places in the network to solve many of today's enterprise security problems? Question 20 of 20. (F) True or false: Antivirus inspection is proxy-based.
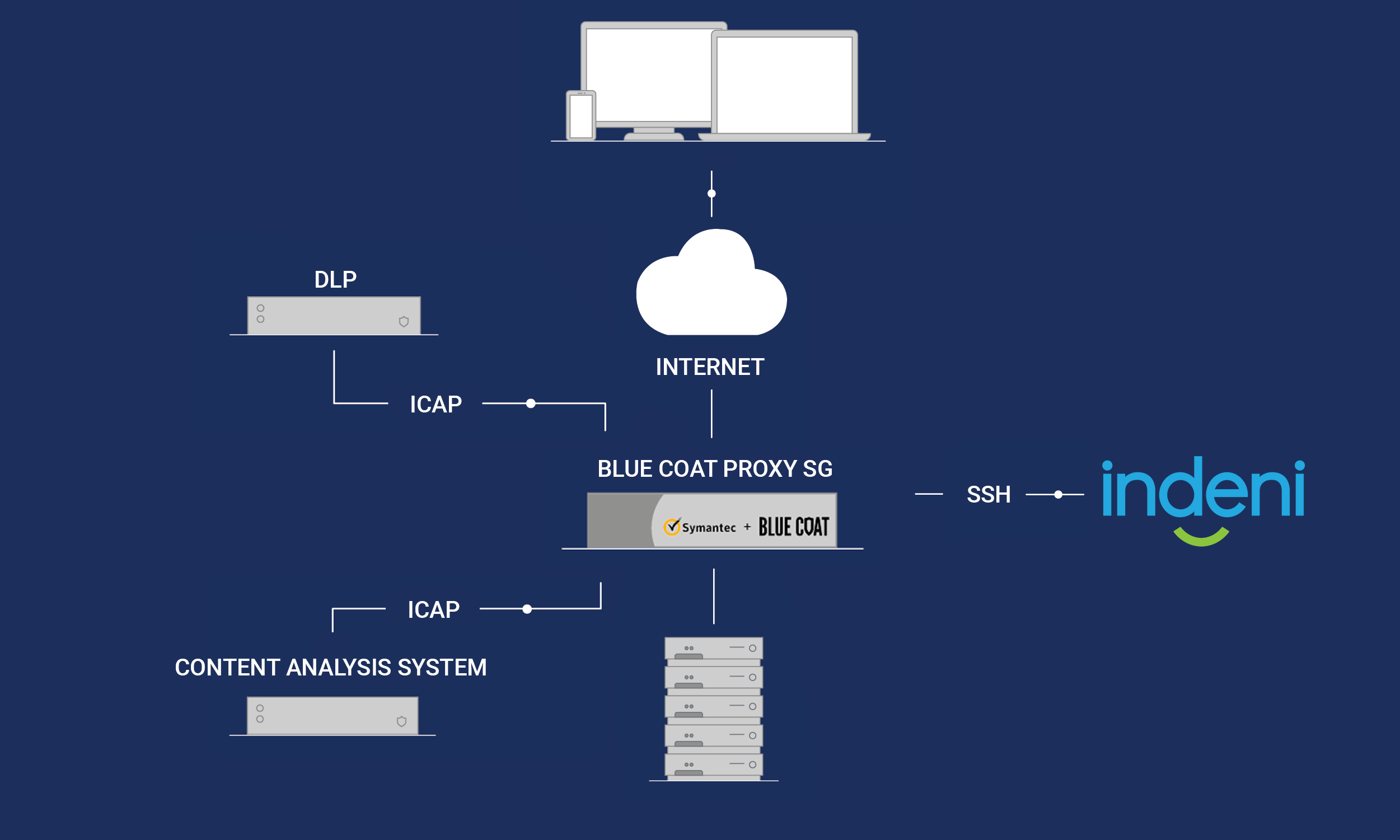
What is a Firewall? | Webopedia Proxy firewalls only inspect Internet traffic from specific protocols. Proxy servers can provide Stateful inspection firewalls permit or drop packets based on the state of an attempted network Palo Alto, widely considered the top of the field, is a nine-time Magic Quadrant Leader at this time of writing.
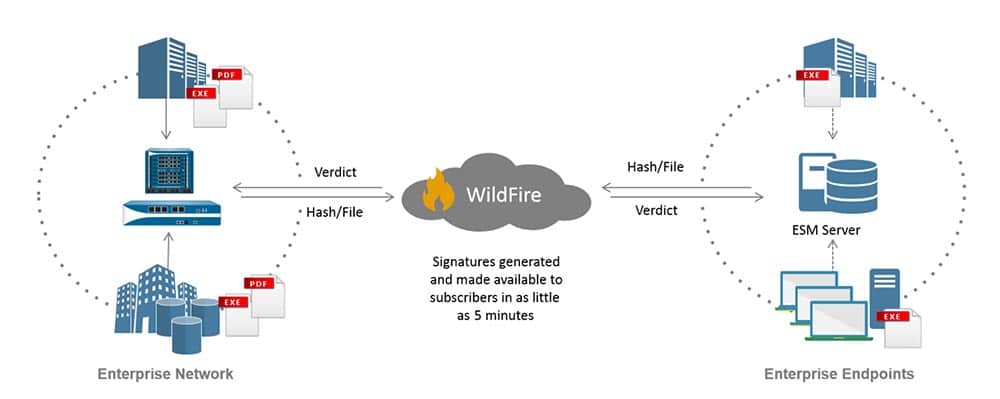
Threat Signature Categories There are three types of Palo Alto Networks threat signatures, each designed to detect different types of threats as the firewall scans network traffic: Antivirus signatures—Detect viruses and malware found in executables and file types. Anti-spyware signatures—Detects command-and-control (C2)...
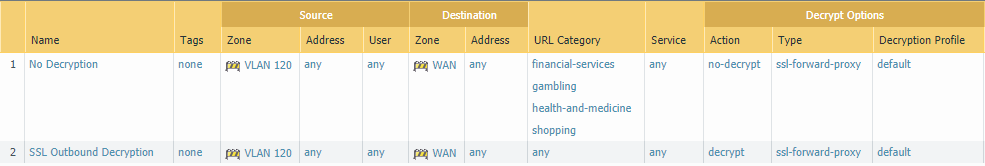
How to Configure URL Filtering on Palo Alto Firewall In this lesson, we will learn to configure URL Filtering on Palo Alto Networks Firewall. Let's get started. The default URL Filtering profile in Palo Alto, blocks the abused-drugs, adult, command-and-control, gambling, grayware, hacking, malware, phishing, questionable, and weapons URL categories.
How to Install and Use Global Protect VPN Client | UMass Amherst Open the App Store and install the Global Protect app by Palo Alto Networks. Once it is installed, launch the app. Type vpn.umass.edu in the portal Address field and tap Connect.
[SOLVED] Fortinet Webfilter Error Page - Firewalls Site-to-Site Palo Alto VPN is Failing Is there such a thing as a firewall/router with cellular backup? You'll want to use the Fortigate's LAN IP address which is 192.168.2.5 based on your post above. With this setup you are more in control of DNS which will hopefully be more stable for you.
Top Threat Intelligence Platforms for 2022: Compare Solutions Palo Alto Networks Cortex XSOAR TIM. LookingGlass Cyber Solutions is an open source-based threat intelligence platform that delivers unified threat protection against sophisticated cyberattacks to global enterprises and government agencies by operationalizing threat intelligence.
Comparing Palo Alto Networks with Proxies Simplified Policy Management: Palo Alto Networks delivers policy-based visibility ... Apply threat inspection to each application ... Anti-virus protection.2 pages
types of PA firewall inspection - LIVEcommunity - 295613 PaloAlto only supports flow based inspection. ... has 2 inspection modes, the base flow mode and the proxy mode, my question is The Palo Alto firewall, ...9 answers · Top answer: Hi @o_hernandez As @MP18 correctly assumes, this is not like it is possible with fortigate ...













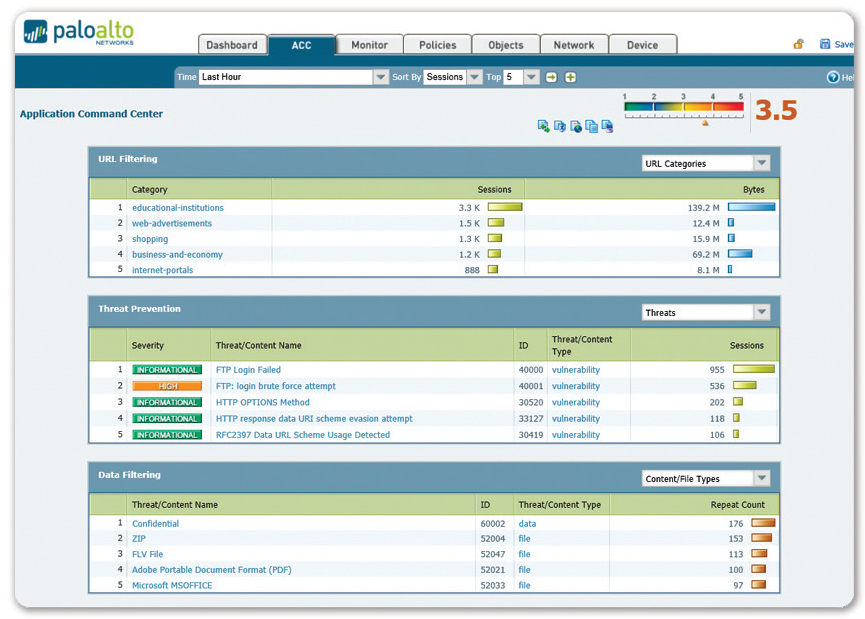

0 Response to "40 antivirus inspection is proxy based palo alto"
Post a Comment