42 antivirus policy in cyber security
Cyber security is a subset of IT security. While IT security protects both physical and digital data, cyber security protects the digital data on your networks, computers and devices from unauthorized access, attack and destruction. Network security, or computer security, is a subset of cyber security. Cybersecurity policy and resilience Cloud security and assurance Digital Geneva Convention Cybercrime legislation and strategy Cybersecurity policy and resilience Increasing cybersecurity in critical sectors is vital to the future of national economies and has become a priority for governments around the world.
What's more, as most cyberattacks tend to exploit basic vulnerabilities in systems, they are easy to prevent with antivirus software, patch updating and staff awareness training. A cyber protection policy means your staff will be better informed and able to take appropriate action to prevent attacks Endpoint security

Antivirus policy in cyber security
Typically, the first part of the cybersecurity policy is focused on the general security expectations, roles, and responsibilities within the organization. The second part may include sections for several areas of cybersecurity, such as guidelines for antivirus software or the use of cloud applications. Cybersecurity. President Biden has made cybersecurity, a critical element of the Department of Homeland Security's (DHS) mission, a top priority for the Biden-Harris Administration at all levels of government. To advance the President's commitment, and to reflect that enhancing the nation's cybersecurity resilience is a top priority for ... AntiVirus | Cybersecurity AntiVirus Antivirus software is designed to find known viruses and oftentimes other malware such as Ransomware, Trojan Horses, worms, spyware, adware, etc., that can have a detrimental impact to the user or device. Antivirus programs provide a way to protect against known threats.
Antivirus policy in cyber security. Cyber security is the practice of defending systems, networks, applications and data from cyber attacks. Cyber security is principally concerned with preventing criminals from accessing, changing, destroying or stealing sensitive data. Organizations also take cyber security measures to prevent theft of funds, extortion, identity theft and ... Antivirus Policy and Procedure Best Practices. Published Date: January 13, 2019. The primary purpose of the anti-virus solution or software is to guard against malicious software or scripts by blocking or quarantining this software that is identified, and alerting administrators that such action has taken place. IT Policies at University of Iowa. University of California at Los Angeles (UCLA) Electronic Information Security Policy. University of Notre Dame Information Security Policy. University of Iowa Information Security Framework. Carnegie Mellon Information Security Policy. Stanford University Computer and Network Usage Policy. A cyber security policy outlines: technology and information assets that you need to protect; threats to those assets; rules and controls for protecting them and your business; It's important to create a cyber security policy for your business - particularly if you have employees. It helps your employees to understand their role in ...
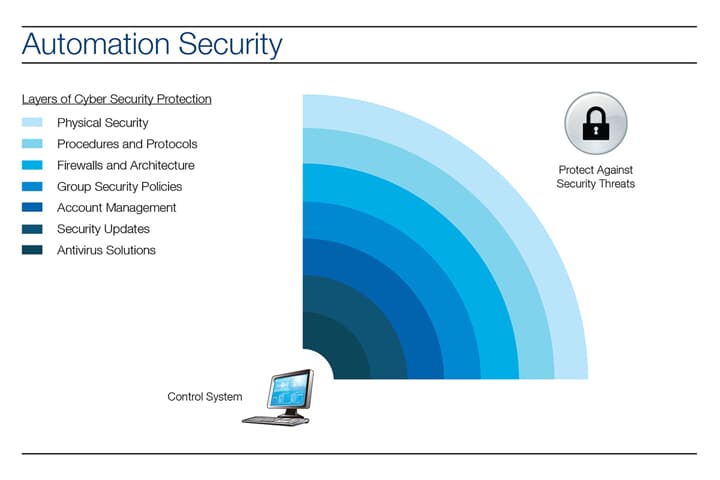
There are some important cybersecurity policies recommendations describe below- 1. Virus and Spyware Protection policy This policy provides the following protection: It helps to detect, removes, and repairs the side effects of viruses and security risks by using signatures. Policy brief & purpose. Our company cyber security policy outlines our guidelines and provisions for preserving the security of our data and technology infrastructure.. The more we rely on technology to collect, store and manage information, the more vulnerable we become to severe security breaches. Information Security Policy Personnel Security Policy Physical and Environmental Protection Policy Security Awareness and Training Policy Protect: Data Security (PR.DS) PR.DS-1 Data-at-rest is protected Computer Security Threat Response Policy Cyber Incident Response Standard Encryption Standard Incident Response Policy Information Security Policy 9 policies and procedures you need to know about if you're starting a new security program Any mature security program requires each of these infosec policies, documents and procedures.
A cybersecurity policy sets the standards of behavior for activities such as the encryption of email attachments and restrictions on the use of social media. Cybersecurity policies are important because cyberattacks and data breaches are potentially costly. At the same time, employees are often the weak links in an organization's security. NordVPN is stepping into the antivirus market with the release of Threat Protection, a new cybersecurity product integrated into the NordVPN app that offers protection against phishing attempts, malicious websites, infected files and other online threats. Specifically, the new offering mitigates three primary kinds of threats: web trackers and ... IT Security Policy 2.12. To enable data to be recovered in the event of a virus outbreak regular backups will be taken by the I.T. Department. 2.13. Management strongly endorse the Organisation's anti-virus policies and will make the necessary resources available to implement them. 2.14. Users will be kept informed of current procedures and ... A company cyber security policy helps clearly outline the guidelines for transferring company data, accessing private systems, and using company-issued devices. Ensure your business has the right security measures in place by creating and implementing a complete cyber security policy.
The Multipoint Group is focused in Cyber Security and Cyber Intelligence. Call our experts of the company in your region: Europe, GCC countries or Israel. We have the solution to every problem or ...
KEY ELEMENTS OF CYBER SECURITY AUDITING: CONTROLS AND THREATS Part of auditing is ensuring that organizations have implemented controls. This means that preventative tools such as firewalls and antivirus software have been put in place. It also means that awareness efforts have been made, and that user education about
26 Cyber Security Statistics, Facts & Trends. Cybercrime comes in many different shapes and sizes, and so do its consequences. What follows is a collection of some noteworthy statistics on the ...
If antivirus mechanisms are disabled, additional security measures may need to be implemented for the period of time during which antivirus protection is not active. Audit Controls and Management On-demand documented procedures and evidence of practices should be in place for this operational policy.
Policy. All computers that are connected to the University of Richmond network must have the standard supported anti-virus software installed and scheduled to run at regular intervals. In addition, the anti-virus software and the virus definition files must be kept up-to-date.
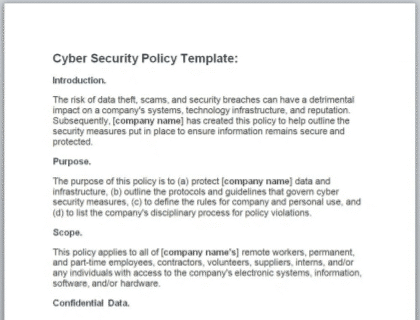
Company cyber security policy template This Company cyber security policy template is ready to be tailored to your company's needs and should be considered a starting point for setting up your employment policies. Policy brief & purpose Our company cyber security policy outlines our guidelines and provisions for preserving the security of our ...
of any cyber security strategy / policy Good cyber security policies and practices put people and their rights at the centre and seek to strengthen and protect human rights as a core objective of the strategy. o Protecting Individuals: Cyber security frameworks must include data protection laws
Cyber Security Policy March 2010 . 2 ... Information security refers to the protection of information from accidental or unauthorized access, destruction, modification or disclosure. Digital information is defined as the representation of facts, concepts, or instructions in a formalized manner suitable for
National Cyber Security and Data Protection Strategy ... This strategy is intended to shape the Government's policy on cyber security, while also offering a rational and compelling vision to share with the public and private sector, civil society, academia and the wider population. ...
A multipronged approach to protect ICT supply chains from cyberattacks. Genie Sugene Gan, Head of Public Affairs for Asia Pacific, Kaspersky. Cyberattacks on Information and Communications Technology (ICT) supply chains are on the rise. This is dangerous as vulnerabilities can be introduced at any phase of the ICT life-cycle, from design ...
This cyber security policy template can be used and customized for your company's specific needs and requirements. Use this Cyber security policy template to set up your company's HR Policies and Procedures. This Cyber security policy template can also help you to stay compliant with specific rules and regulations.
AntiVirus | Cybersecurity AntiVirus Antivirus software is designed to find known viruses and oftentimes other malware such as Ransomware, Trojan Horses, worms, spyware, adware, etc., that can have a detrimental impact to the user or device. Antivirus programs provide a way to protect against known threats.
Cybersecurity. President Biden has made cybersecurity, a critical element of the Department of Homeland Security's (DHS) mission, a top priority for the Biden-Harris Administration at all levels of government. To advance the President's commitment, and to reflect that enhancing the nation's cybersecurity resilience is a top priority for ...
Typically, the first part of the cybersecurity policy is focused on the general security expectations, roles, and responsibilities within the organization. The second part may include sections for several areas of cybersecurity, such as guidelines for antivirus software or the use of cloud applications.





![PDF] Cyber Security Curriculum Development: Protecting ...](https://d3i71xaburhd42.cloudfront.net/56842078f8fd97edb1e5c4e15d7218ebc879eeec/8-Table1-1.png)
























0 Response to "42 antivirus policy in cyber security"
Post a Comment